Cloud technology has undoubtedly become an indispensable aspect of computing in recent years. Nevertheless, some small- to mid-sized businesses (SMBs) still face uncertainty when deciding which processes to migrate to the cloud. If you own or operate an SMB and are facing this dilemma, we’ve got you covered.
Will IT support be replaced by AI?

All this talk of AI can make your mind go haywire
With headlines like ‘Don’t bring children into this AI world’ and the fact that I have just watched an online news report hosted by a very life-like AI-generated newscaster it makes one wonder, where to next?
Doctors are using AI to assist with speedy diagnoses, the picture at the top of this article was created with AI. In the words of the jealous girlfriend in The Sound of Music, ‘my dear, is there anything you can’t do?!’
As we are all being made acutely aware, AI is extremely useful and can often do things better than we can.
Unveiling the invisible threat: Exploring the world of fileless malware

With its ability to evade traditional antivirus solutions, fileless malware poses a significant challenge to organizations and individuals alike, as it can cause severe damage without leaving any traces behind. In this article, we will delve into the intricacies of fileless malware, explore how it works, and discuss effective strategies to protect against this invisible threat.
Boost collaboration and productivity with Microsoft Delve
Why hybrid cloud solutions matter

Hybrid cloud solutions are becoming increasingly popular because they offer numerous benefits to businesses of all sizes. By combining the capabilities of both the public and the private cloud, organizations can leverage the strengths of each cloud environment to create a versatile and scalable infrastructure.
Don’t end up like these poor phish

A report released in May this year has found that though spear phishing emails only account for 0.1% of email based attacks, they are responsible for two-thirds of all breaches. Conducting extensive research by analysing 50 billion emails from 3.5 million mailboxes across 1350 organisations, which included about 30 million spear-phishing emails, half of these organisations had succumbed to a spear-phishing attack in 2022.
Of those who experienced a breach due to a spear phishing attack 55% had machines infected with malware or viruses and about half had sensitive data or login details stolen.
Voice AI – What you need to know
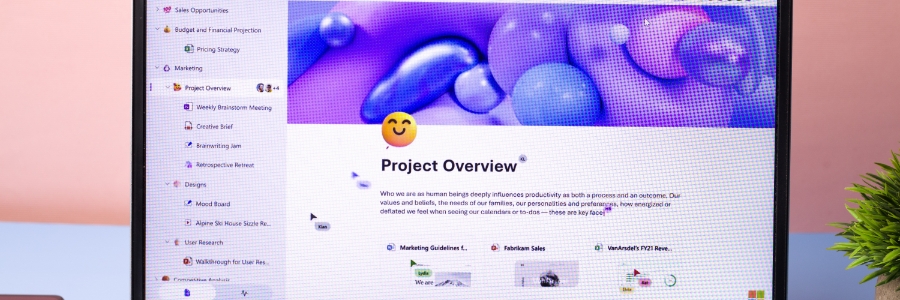
Getting started with Microsoft Loop: A beginner’s guide for Outlook and Teams
Forewarned is Forearmed – A hacker who’s who

In the dangerous landscape we navigate on the digital frontier, the more we know about our enemies, the better. Let’s go behind the lines (of code) to learn more!
‘Hacker’ – this word conjures up images of mean looking characters lurking over keyboards, leering at multiple code-laden screens and wreaking havoc on the internet.
When to use Groups, Teams, and Yammer

In the digital age, businesses and organizations have a variety of collaboration tools at their disposal. With so many options available, it can be challenging to determine which tool is best suited for specific tasks and goals. Three commonly used tools in the Microsoft ecosystem are Groups, Teams, and Yammer.